Trust is fundamental to everything we do. Without it, we are lonely islands of individuals. With it, we have the potential for a better connected world. So with over half of the world’s 7.5bn people now online, who can we really trust in the digital world today? And how is the trust erosion we’re constantly experiencing today going to reverse? Read on if you care to understand how your information is being exploited and profited from by even so-called ‘good guys’ while you are being put needlessly at risk. It must and can radically change in all our lives.
It’s not just Equifax and Yahoo.
Identity theft is at an all time high and the daily news has become a consistent reminder that every online citizen is at risk every day. Just last week the FDIC were shown to have been hit with over 50 (!) breaches in 2015/16 that exposed hundreds of thousands of American’s personal information. Worse still they admitted it was taking more than 9 months on average to even notify those affected.

Depressingly, the Equifax breach hammers home this point once again. The scope and scale of the breach is mind-boggling. 145 million Americans, or about 45% of the population’s social security numbers, birthdates, driver’s license numbers and addresses were exposed (click to tweet). And, at the same time, it’s mundane. Equifax is just one more name in the long list of identify theft incidents and data breaches.
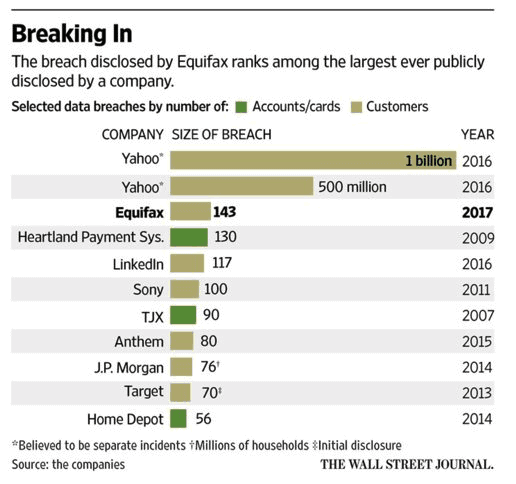
It’s a pandemic. And yet even as the WSJ reported these facts a week ago they were wrong by a factor of 3. We don’t even know what we know!
Sadly, I have watched these problems grow for nearly 3 decades having been involved with Symantec from the early days. Yet, I stopped investing in security over the last decade. Why? Because in diligence with those in the know from CIOs to top experts, it became repeatedly clear that “There are only two types of companies” ex-FBI director Meuller said, “Those that have been hacked and those that will be hacked.” But we beg to differ.
There are only two types of companies — those that have been hacked and those that are aware of it. (click to tweet)
(Just this past week Deloitte acknowledged a lack of basic security measures exposed large databases of clients’ secret emails and several gigabytes were exfiltrated by hackers who had free reign in the network for a “long time”. The extent of the breach is yet unaccounted for — ironic for an accounting firm we are expected to trust as an auditor! And I’m not picking on Deloitte, they’re just the current example.)
It’s not hard to conclude that that an even sadder problem is:
Even for those who have been hacked, they rarely know the extent of the damage or can report it fast enough.
(Yahoo originally reported 1 billion accounts were breached and now just revealed ALL 3 BILLION of their accounts were! )
But the problem is no longer just security, it’s reliability, dependability and ultimately trust throughout our (fake?) news, records, communications, collaboration and transactions. Take the simple example of buying a house:
Why is it we can’t even rely on the title of a house and have to take insurance on it in a purchase transaction?
(ALTA has reported as many as ⅓ of all transactions having problems.)
What can be done about this? How is this all about to change, and why have we decided to devote a major part of our investing to this area after studying it for years? And where will we invest and why?
Simple and complex — what’s the essence?
Digital trust is simple and complex all at the same time. At the absolute simplest level, it’s always better to have a prevention than a cure.

And in the worst case even if we wonder what happened (!) it’s good to have insurance. But of course that’s not cheap.

As a result, cybersecurity has become a game of thinner and more complex layers of defense fueled by failure in the weakest links without enough fundamental change. There’s been a ton of innovation from great companies like Palo Alto Networks, but still it’s a game of layers. And recently with the problem of not even knowing you’ve been hacked until after the fact, has come the the challenge of cleaning up the mess (!) creating a need for “Incident Response.”

(Former Symantec team member John Bruce envisioned and built a valuable Incident Response business in the middle of this — Resilient Systems, and it was snapped up by IBM last year.)
Clearly there’s a lot of money to be made in all of this — but is it all just an unnecessary overhead? What if we wanted to get to a different place where we can have just one pre-emptive word instead of billions of dollars of spend? The word of course is Trust.
This is where it can get complex, but again for the purposes of (over) simplification, let’s think of our digital world very personally. If we choose to store or access our information digitally or online we’ve been trained to use a password, and if we’re diligent we use a strong and changing one and manage it in a central password manager. Then maybe a few of us even back up our information. Then as we share our information to communicate, collaborate, or conduct transactions, we use those passwords, and yet knowingly or unknowingly, our digital footprint expands and so does the potential “attack surface” along with it, as well as the network of people who can become hackers or bad actor attackers themselves.
Your are not just being exposed, you are being exploited.
If you have an online email account, a social media account, an online bank account, or any of the other myriad of cloud services available to manage your life, you may be aware of how many separate entities that have access to your personal data. What you might not be aware of is that there are thousands of other data brokers like Equifax that are capturing, saving and profiting from your information and I’ll bet you’ll be unaware of most of them and have no actual business relationship with.
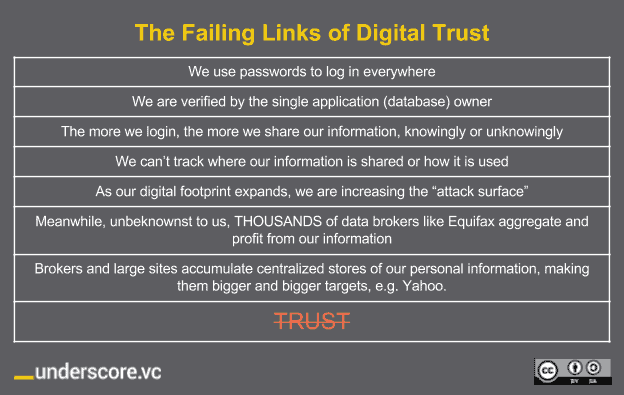
This is a chain of information where the weakest link makes the rest of the chain untrustworthy and where you can’t track who does what with your Personally Identifiable Information (PII).
The current system of trust is forcing us to fail and be profited from.
As individuals, we are forced to log on and trust everywhere if we want to transact or even just communicate online. Now increasingly, these incidents are helping us to realize the degree to which this trust is both blind and, more and more apparently every day, just plain unfounded.
Suddenly, everyone from your mother to your accountant needs to be concerned about whether or not all of the organizations have appropriate security controls in place. Are their systems up to date? Are they secure? Have they updated the latest security patches? How can you verify that they are actually secure? And even if they are, what have they done with your information?
To be clear, this is a breakdown in trust. A complete failure in digital trust. In the absence of trust in the systems that manage our digital personal information, the current architecture of web applications often pushes the problem of security and trust to the weakest link in the chain — and when the chain breaks, as it did with Equifax or Yahoo or Deloitte or (insert your favorite example), the first person in the chain (You!) is/are forced to carry the burden or the last person in the chain becomes responsible for addressing an issue over which they may have limited understanding or traceability even if they are culpable. And don’t even get me started on the challenges of the expected trillion Internet of Things (IoT) in our homes like baby monitors that can turn out to be the weak link. One of our prior investments, Dyn, learned first hand the havoc that they can wreak as they brought down much of America’s internet last year.
The burden of protection has therefore been pushed to the individual to protect herself from the failings of others. How is this even realistic or possible? [Hint: It’s not today, but it can be…]
Using our simple framework above, if we’re going to preemptively take charge of this breakdown we need to create an immutable chain of digital trust (a la blockchain) where we can keep ownership of our information that can be verified and tracked wherever and whenever it is used. (click to tweet)
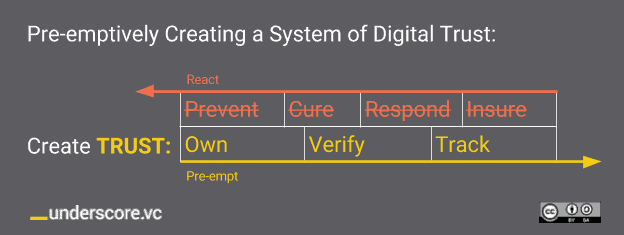
This is purposely oversimplified because as Einstein famously said:
You do not really understand something unless you can explain it to your grandmother.
Many people from our Blockchain Core Community of security, cryptography, economics and even game theory experts have weighed in to simplify and reimagine a solution with us. If you would like to learn more about how we can change this for the better, read on:
Part 2: Preemptively Creating a System of Digital Trust
Part 3 — After the Bust: Building Out Blockchain Technology.
Part 4 — 3 Investment Criteria to Qualify a Blockchain Project
Written with contributions by Bryan House, Ben Jones, Michael Skok and our Core Community.